Application Security
Most of the cyber attackers target the vulnerabilities in the application layer. With the enhanced complexity of the application tier, it is essential to test applications for their security. Application security can be ensured by constantly tracking the headers, by checking for any malware injections, defacement attacks, and much more. Here are a few checks that Digital Risk Analyzer will run to ensure that your application is secure.
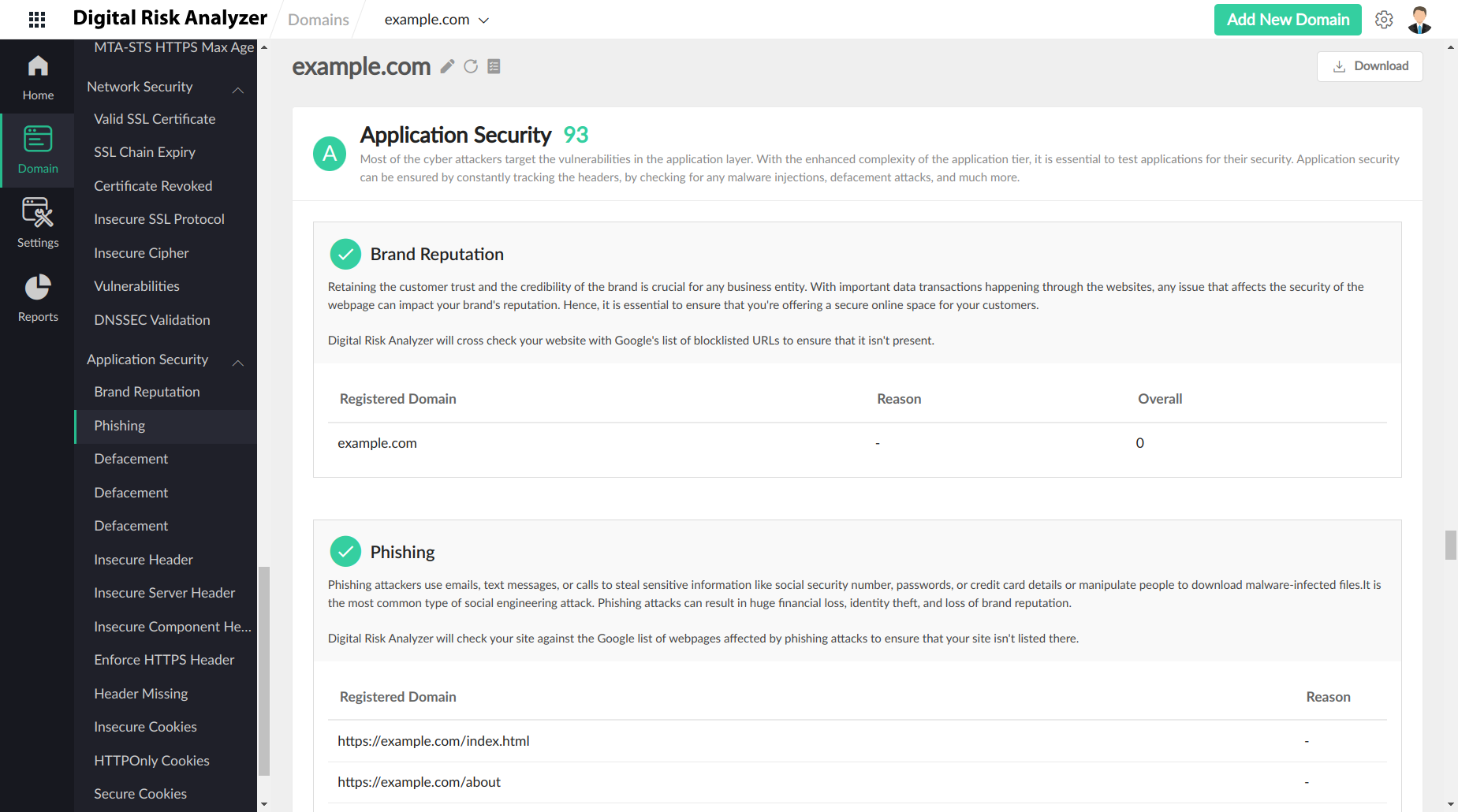
Brand Reputation
Retaining the customer trust and the credibility of the brand is crucial for any business entity. With important data transactions happening through the websites, any issue that affects the security of the webpage can impact your brand's reputation. Therefore, it is essential to ensure that you're offering a secure online space for your customers. Digital Risk Analyzer will cross check your website with Google's list of blocklisted URLs to ensure that it isn't present.
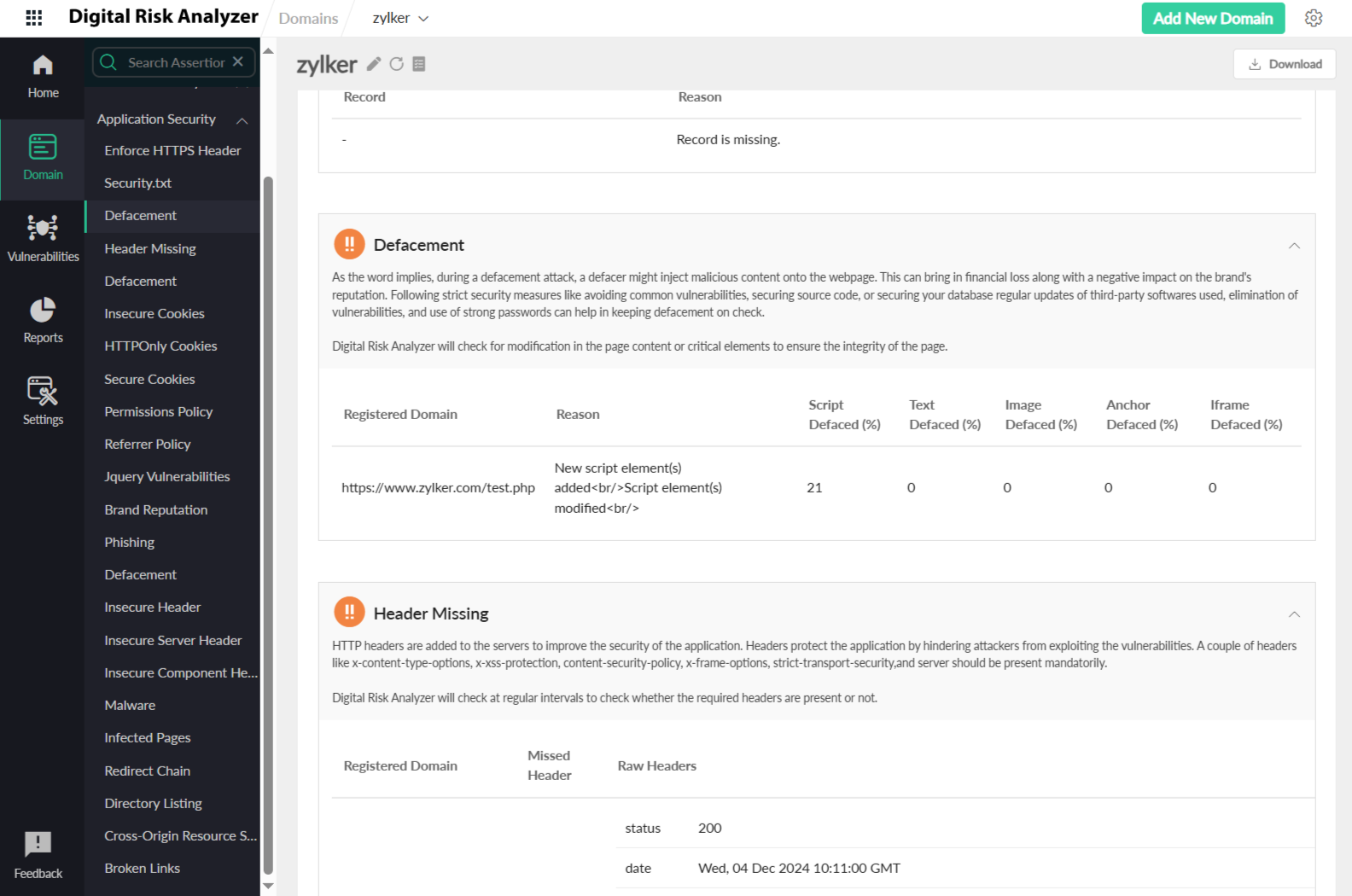
Defacement
As the word implies, during a defacement attack, a defacer might inject malicious content onto the webpage. This can bring in financial loss along with a negative impact on the brand's reputation. Following strict security measures like avoiding common vulnerabilities, securing source code, or securing your database regular updates of third-party softwares used, elimination of vulnerabilities, and use of strong passwords can help in keeping defacement on check. Digital Risk Analyzer will check for modification in the page content or critical elements to ensure the integrity of the page.
Malware
Malware refers to any malicious files that can harm a network, or a service, and can be a potential threat to end users. The malicious files might be used in different forms like advertisements, email attachments, phishing emails, and text messages. Slower performance, numerous pop-ups blocking your screen, browser redirections, or infection warnings can imply that your machine has been compromised. This can expose your valuable credentials to cybercriminals. Digital Risk Analyzer will perform a client-side malware scanning strategy where the pages will be crawled to extract all the files available on each page. After which, these pages will be scanned and checked for malicious content.
Infected Pages
Pages which contain more than one malware-infected file will be deemed as infected pages. Infected pages can be used by attackers to steal highly sensitive data or other credentials. It is important to ensure that your pages aren't infected. Digital Risk Analyzer will run regular checks to ensure that your files or pages are secure.
Phishing
Phishing attackers use emails, text messages, or calls to steal sensitive information like social security number, passwords, credit card details, or manipulate people to download malware-infected files. It is the most common type of social engineering attack. Phishing attacks can result in huge financial loss, identity theft, and loss of brand reputation. Digital Risk Analyzer will check your site against the Google list of webpages affected by phishing attacks to ensure that your site isn't listed there.
Insecure Cookies
Cookies are small texts sent by the site you visit to your browser. If the cookie isn't configured properly or if the transport security setting isn't configured correctly, any hacker can access sensitive data stored in the cookies. This is possible even if you own a valid SSL certificate. Digital Risk Analyzer will regularly check the cookies to ensure that they are configured correctly.
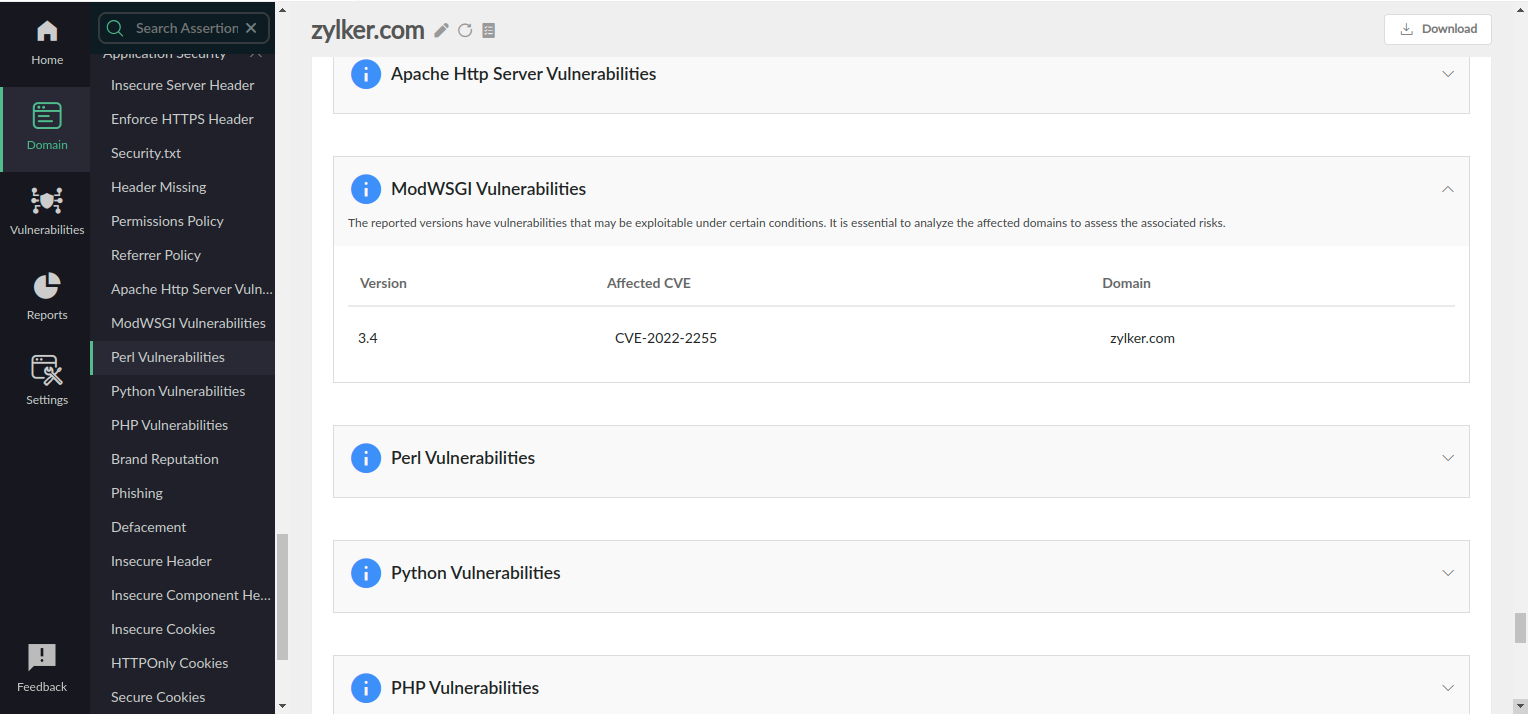
Vulnerabilities
CVE errors are publicly disclosed vulnerabilities that attackers can exploit to compromise software. These flaws can stem from coding issues, misconfigurations, or outdated components. Regular updates and prompt patching are essential to mitigate risks and maintain security. Along with the other assertions, some of the commonly detected CVEs are:
- Apache HTTP Server vulnerabilities
- Pear vulnerabilities
- Python vulnerabilities
- PHP vulnerabilities
- jQuery vulnerabilities
- jQueryUI vulnerabilities
- Chart.js vulnerabilities
- Knockout.js vulnerabilities