Identifying OWASP Top 10 using Digital Risk Analyzer
Identify risks based on severity, evaluate them, and prioritize addressing them based on their position in the Open Web Application Security Project (OWASP) Top 10. Classifying assertions in Digital Risk Analyzer based on OWASP Top 10, you can enhance the security of your software framework.
Use cases
The Digital Risk Analyzer automatically tags security assertions in line with OWASP Top 10 guidelines so users can address real-time critical vulnerabilities, such as injection flaws and broken authentication, to ensure prompt resolutions and enhanced security.
With tagged assertions, vendor domain owners can highlight common vulnerabilities like XSS, ensuring compliance with industry standards, and fostering client trust by demonstrating a commitment to secure vendor domains against common threats.
Accessing OWASP through Digital Risk Analyzer
You can access OWASP by following these steps:
- Log in to Digital Risk Analyzer.
- Add a domain to the Digital Risk Analyzer to initiate the security assessment.
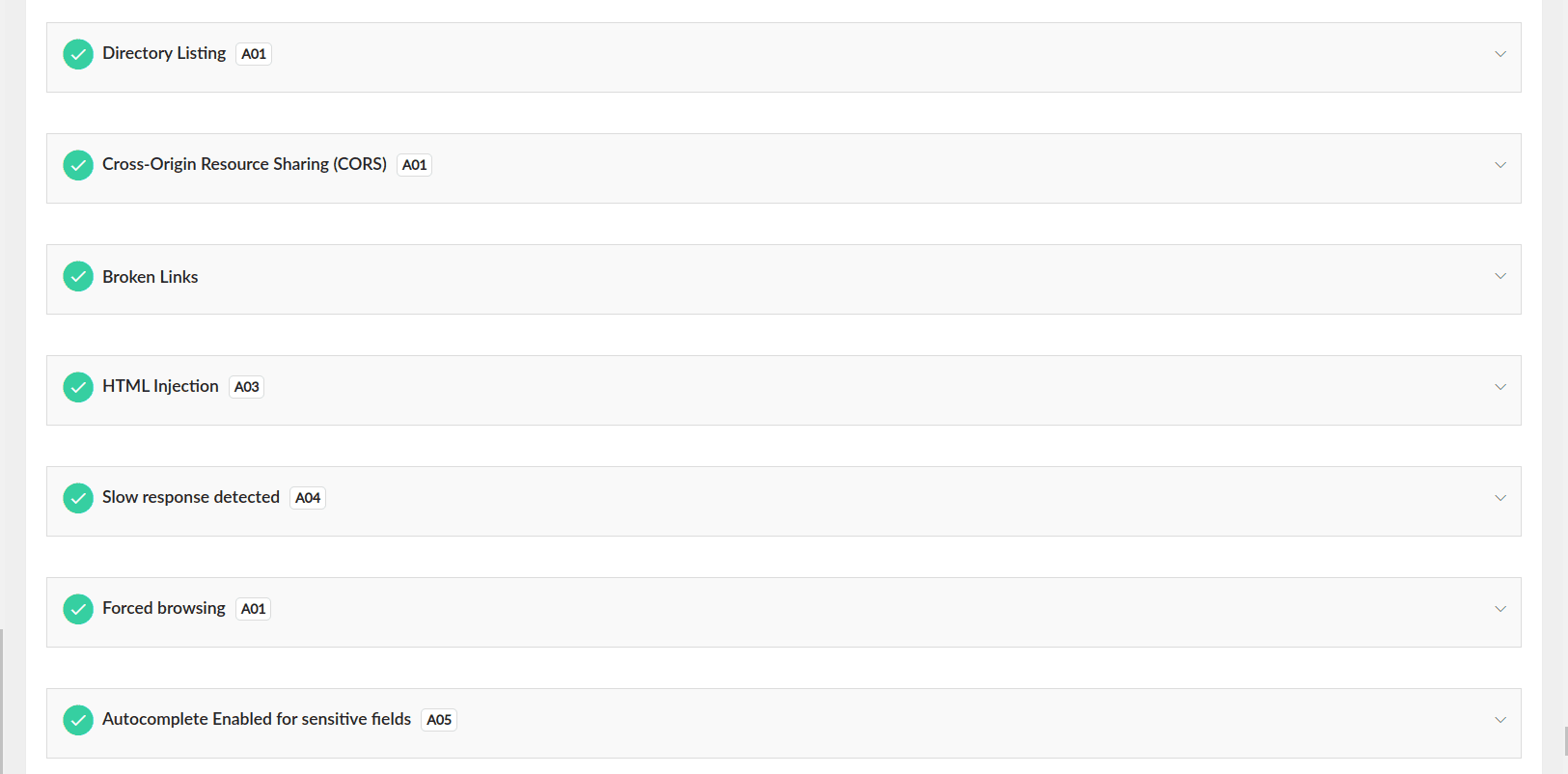
- The domain undergoes a comprehensive list of assertions designed to identify any vulnerabilities or security loopholes.
- Once the assertions are completed, they provide detailed findings on domain-level security issues.
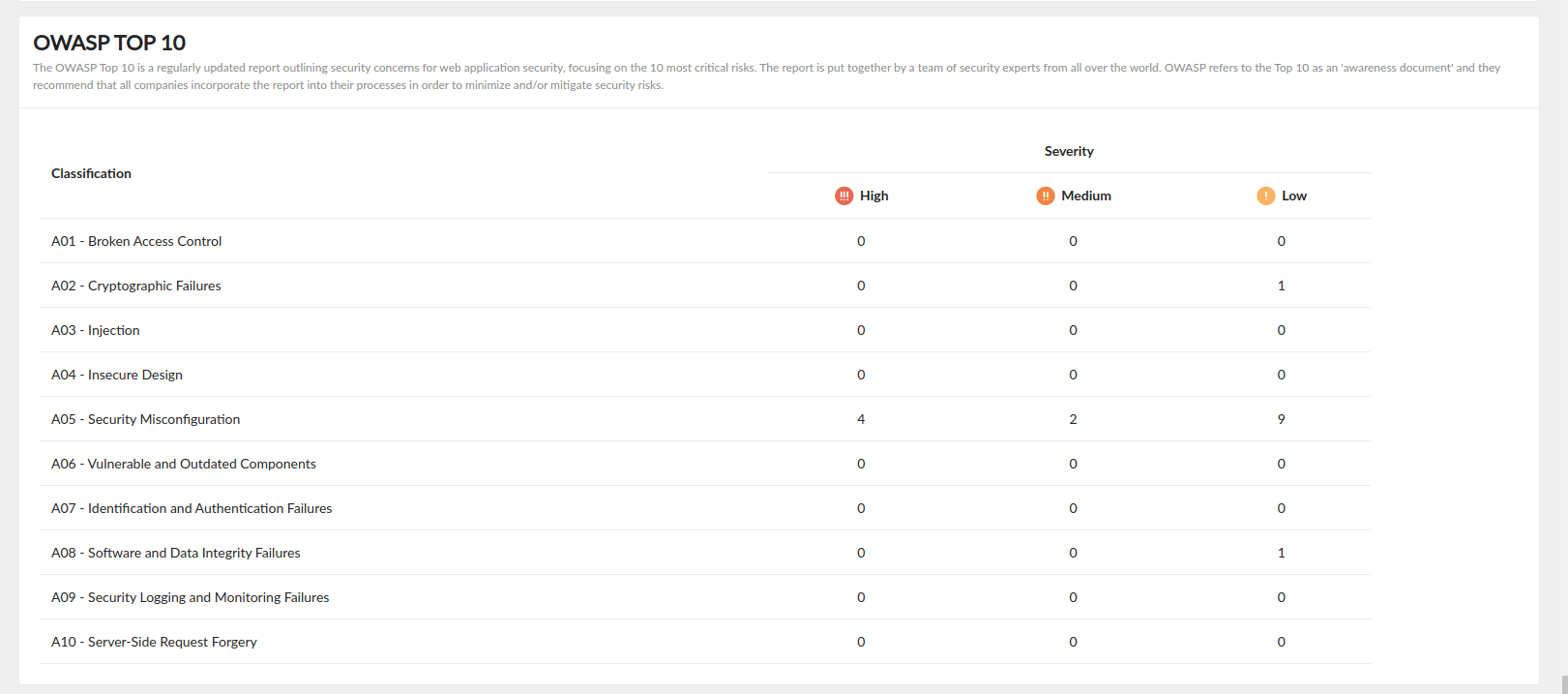
- The Domain Summary provides the results of all completed assertions, detailing the severity of identified vulnerabilities or security issues at the domain level.
- Some assertions are tagged with identifiers such as A01, A02, A03, etc., which indicate the OWASP category they align with.
- Scroll down through the Domain Summary to locate the OWASP summary.
OWASP summary
Once vulnerabilities are identified through assertions, Digital Risk Analyzer generates a comprehensive OWASP summary that provides users with key insights. The summary categorizes vulnerabilities under the OWASP Top 10, delivers detailed descriptions and severity assessments. It guides users with practical remediation
strategies and highlights the importance of addressing these vulnerabilities for compliance and risk management.