Resolve issues faster in your containerized environment by monitoring Kubernetes with Site24x7.
Fundamentals of Kubernetes Security
Kubernetes orchestrates and manages many containers that package multiple applications. A cyberattack on Kubernetes can potentially cripple numerous applications. So, it is critical to secure Kubernetes components.
One of the prevalent security concerns has been misconfigurations. Misconfigurations occur when Kubernetes administrators unintentionally assign incorrect or inappropriate values to fields and keys. Misconfigurations compromise and jeopardize the health of Kubernetes clusters.
There are many tools and measures that can be implemented to protect Kubernetes components and resources. In this article, you will learn the basics of Kubernetes security, starting with misconfigurations and covering security tools such as Kubescape and Kubeval.
Kubernetes Misconfigurations and Vulnerabilities
Kubernetes manifests are written in YAML, a language comprising maps and key-value pairs. Maps are essentially ordered segments of key-value pairs, which assign and define values used to configure Kubernetes. If a crucial property such as a livenessProbe is not added, this leads to a misconfiguration–the liveness probe catches deadlocks and notices the kubelet when an application is failing.
Misconfigurations are created when an important value is not added or an incorrect value is set. Another example would be setting the allowPrivilegeEscalation property to true. This property will enable hackers to manipulate the host machine in the case of a security breach.
There are many misconfigurations in Kubernetes that lead to vulnerabilities that can be exploited by hackers. If the ingress or egress are not set, this will allow hackers to penetrate your cluster since there will be no rule to filter incoming and outgoing traffic. You can use tools such as Kubescape, Datree, and many more to spot clusters and manifest misconfigurations conveniently. You will learn more about these tools in the following sections.
Kubernetes Policies
Kubernetes Policies are the best rules to enforce during Kubernetes development. These policies block resources and objects that do not comply with your security standards from being applied to your cluster. Kubernetes Policies give you the power to choose what users can apply to your cluster.
Organizations can adopt free tools such as Kyverno to enforce Kubernetes policies. Kyverno has a CLI and Kubectl plugin that can be downloaded using Krew. This command line allows you to apply policies using the kyverno apply command. In addition, Kyverno lets you mutate and generate resources.
This is just one of the many tools that make Kubernetes better and easier to use every day.
Kubernetes Security Tools
Cloud-native security companies such as ARMOSEC and Aqua Security have been releasing several tools dedicated to optimizing Kubernetes security. These solutions detect misconfigurations and vulnerabilities and provide ways to remediate them.
It is crucial to adopt and set up security tools in your Kubernetes workflow. We will discuss a few security tools below.
Kubescape
This is a free CLI security tool that scans your clusters looking for vulnerabilities. The command line will either output the results in PDF or through the terminal. Kubescape provides security details, including:
- Risk level of detected vulnerabilities
- Kubernetes components that have been affected by the vulnerability
- Documentation of the vulnerability
- Solution to the detected vulnerability and any other remedies
The Kubescape documentation contains all the resources and instructions you need to install Kubescape on your favorite operating system. After installation, use the following command to scan your cluster. The —-format flag dictates the output format of the scan results, which in this case will be PDF:
$ kubescape scan --format pdf --output scan-results.pdf
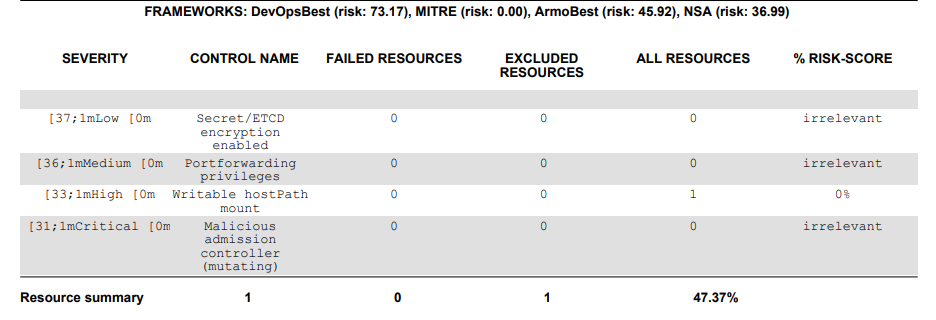
You will receive an output similar to that seen below– a list of detected vulnerabilities. The table will provide you the severity of each vulnerability for you to resolve based on criticality. The control name column shows you the Kubernetes component being scanned, while the other fields offers you a summary of scanned results in terms of risks and which resources failed:
Datree
Misconfigurations from not setting resource limits are common in Kubernetes developments. Datree scans local YAML files and provides details of misconfigurations found and ways to resolve it. Datree has a free CLI that is available in different operating systems. It can also be integrated into your CI/CD pipelines.
Visit the Datree documentation page to learn how to install it on different operating systems.
The following command scans a manifest:
datree test your-service.yaml
If your manifest has misconfigurations, Datree will detect them and give you the details:
[X] Policy check
❌ Prevent Service from exposing node port [1 occurrence]
- metadata.name: my-service (kind: Service
💡 Incorrect value for key `type` - `NodePort` will open a port on all nodes where it can be reached by the network external to the cluster
Kubeval
This free command line tool validates YAML manifests and scans your local manifests for errors. The Kubeval documentation provides necessary information to install it and it is available on Windows, MacOs, and Linux. You can then use the following command to validate your YAML files:
kubeval secret-reader.yaml
ValidKube
This free online tool validates, cleans, and audits YAML files. If you provide your manifest to the ValidKube website, it will give you an audited and cleaned YAML file within seconds.
ValidKube uses various tools such as Trivy and Polaris to perform the security audit. It is convenient because you don't have to download any files or CLI to use it:
Role-Based Access Control
Kubernetes is used to orchestrate several containers carrying multiple applications developed and maintained by different developer teams. This can lead to certain developers accessing resources such as secrets they are not supposed to view. Therefore, it is imperative to be selective about who accesses specific Kubernetes cluster resources.
To solve this resource access issue, you can use the role-based access control mechanism, enabling you to allow or block different users from accessing various resources. This mechanism consists of Roles and RoleBindings, which are applied at namespace levels. Roles state the rules and permissions that will be applied to a resource like services or deployments. A RoleBinding gives specified user permissions stated in a Role.
Here’s an example of a Role that will be applied to the production-space namespace. This Role permits a user to get, watch, and list deployment resources:
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: production-space
name: deployment-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["deployments"]
verbs: ["get", "watch", "list"]
Use the following command to create the above Role:
kubectl create -f deployment-reader.yaml -n production-space
You will get the following output:
role.rbac.authorization.k8s.io/deployment-reader created
The command shown below binds the previous Role with the default user. The RoleBinding is called deployment-access:
kubectl create rolebinding deployment-access --role=deployment-reader --serviceaccount=foo:default -n production-space
After creating the RoleBinding, use the following command to get the details of the RoleBinding you just created:
kubectl get rolebinding deployment-access -n production-space -o yaml
You will get the following output:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: "2022-07-25T22:16:18Z"
name: deployment-access
namespace: production-space
resourceVersion: "21350"
uid: 36ba6939-e546-48a2-90f4-262ee7c755a8
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: deployment-reader
subjects:
- kind: ServiceAccount
name: default
namespace: foo
Kubernetes Security Best Practices
When it comes to Kubernetes security, it is best to follow some well-known best practices:
- Stay updated: Most of the Kubernetes updates being released contain critical security patches. Always update Kubernetes accordingly.
- Encrypt secrets and passwords: While using third-party tools like Doppler, note that secrets are not encrypted by default.Kubernetes users within your organization who have access to the etcd can copy secrets and use them inappropriately if not encrypted.
- Monitor for vulnerabilities: It’s imperative to consistently fetch logs using tools such as K9s and Sematext, as well as discover new vulnerabilities that hackers target. This will help you detect vulnerabilities before hackers can exploit them.
- Implement firewalls: These prevent unauthorized users from accessing Kubernetes resources; firewalls will protect your cluster by blocking unwanted traffic.
Conclusion
The key to maintaining the security of Kubernetes clusters is continuously testing components, scanning your cluster with tools like Kubescape, and analyzing logs. When you detect misconfigurations, solve them as soon as possible; do not underestimate any vulnerability because there are cyberattackers searching for vulnerabilities and benefiting from the security mistakes made by Kubernetes administrators and DevOps engineers.