Collecting CloudTrail logs using the Lambda Function
CloudTrail logs provide details about all account related activity across your AWS environment. Collecting this historical data helps simplify security analysis and troubleshooting. Read on to learn how to monitor your CloudTrail logs with Site24x7. Learn more about log management with Site24x7.
Create a Log Profile
To collect the CloudTrail logs you will first need to create a Log Profile. Navigate to Admin > AppLogs > Log Profile > Add Log Profile, and follow the instructions below:
- Profile Name: Enter a name for your Log Profile.
- Log Type: Choose CloudTrail logs. If you haven't enabled CloudTrail logs in your AWS account, please follow the instructions given here.
- Log Source: Choose Amazon Lambda.
- Timezone: Select a timezone for your logs.
- Click Save.
- Configure the Lambda function as described here.
Configure CloudTrail logs
- Log in to the AWS console and choose CloudTrail from the Services drop down.
- Click on Trail, and choose Create Trail.
- Create Trail: Provide a name for the CloudTrail service, and choose whether the logs have to be delivered to all regions.
- Management events: Choose the operations that can be performed on your AWS resources.
- Storage location: Create a new S3 bucket, or choose an existing S3 Bucket to which the logs will be sent for storage.
Configure the Lambda Function
- Choose Lambda from the Services drop-down list, and choose Create Function. Select Author from scratch, define a name for the function, and choose Python 3.7 as the Runtime.
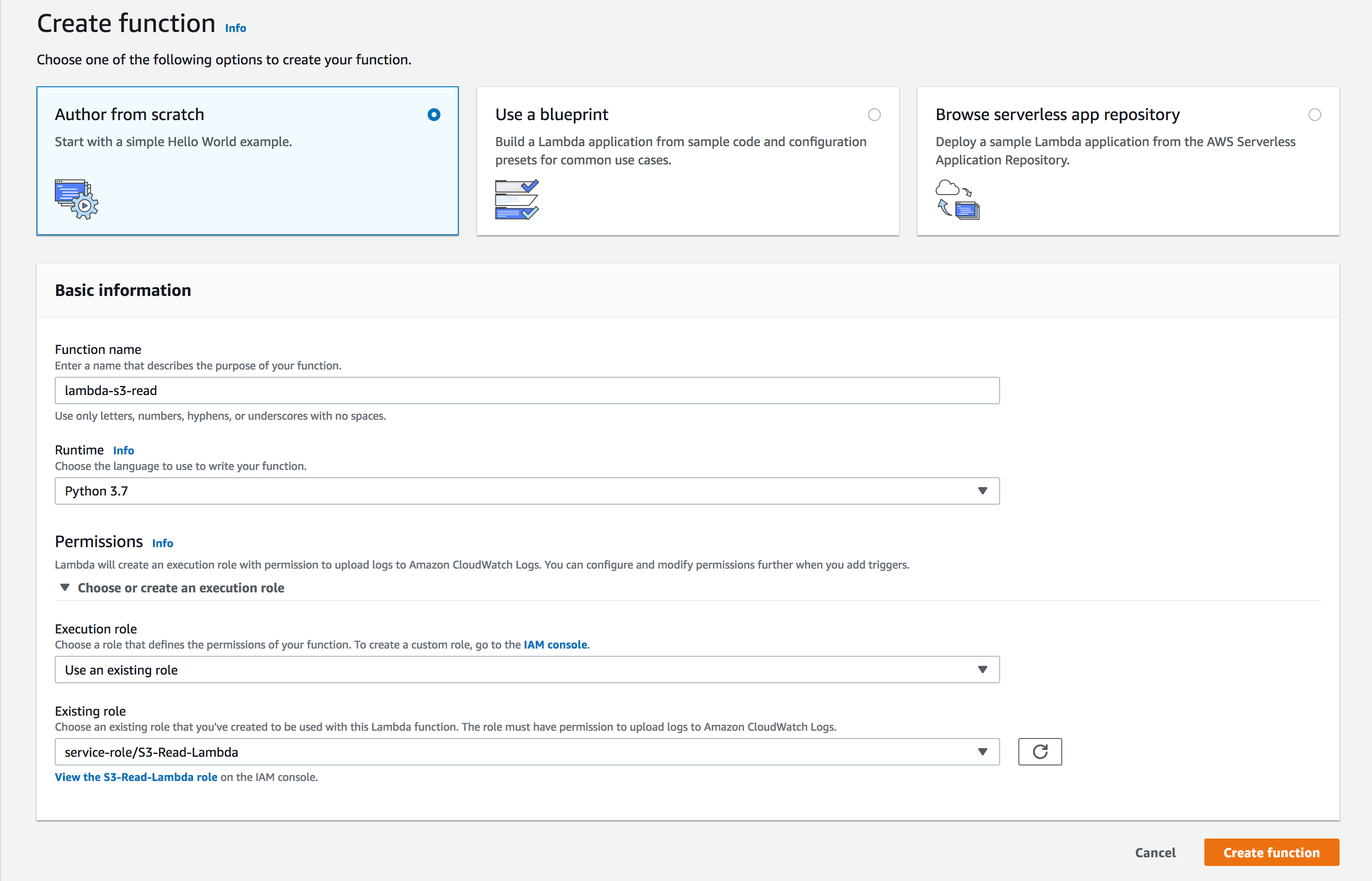
- Permissions: You can choose an existing IAM role or create a new role from the AWS Policy Template. From the Policy Template drop-down select Amazon S3 Object Read-only permission, and enter a role name. You also have the option to create a new user role and extend permission to other services as well.
- Add triggers: Scroll down to choose S3 Bucket. Any log file added to the S3 bucket will be sent to Site24x7 by the Lambda Function.
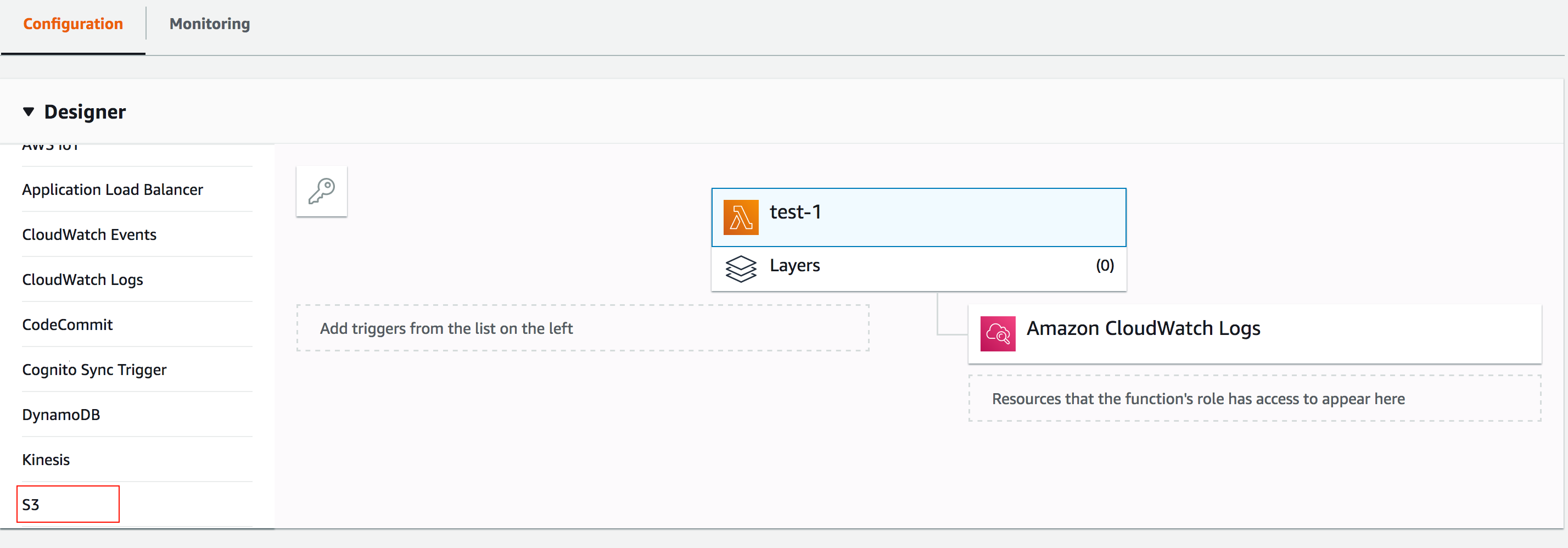
- Configure Triggers
- Bucket:Enter the name of the S3 bucket from which logs will be collected.
- Event type: Choose All object create events.
- Click Add.
- In the window that opens, click on the Lambda Function as shown:
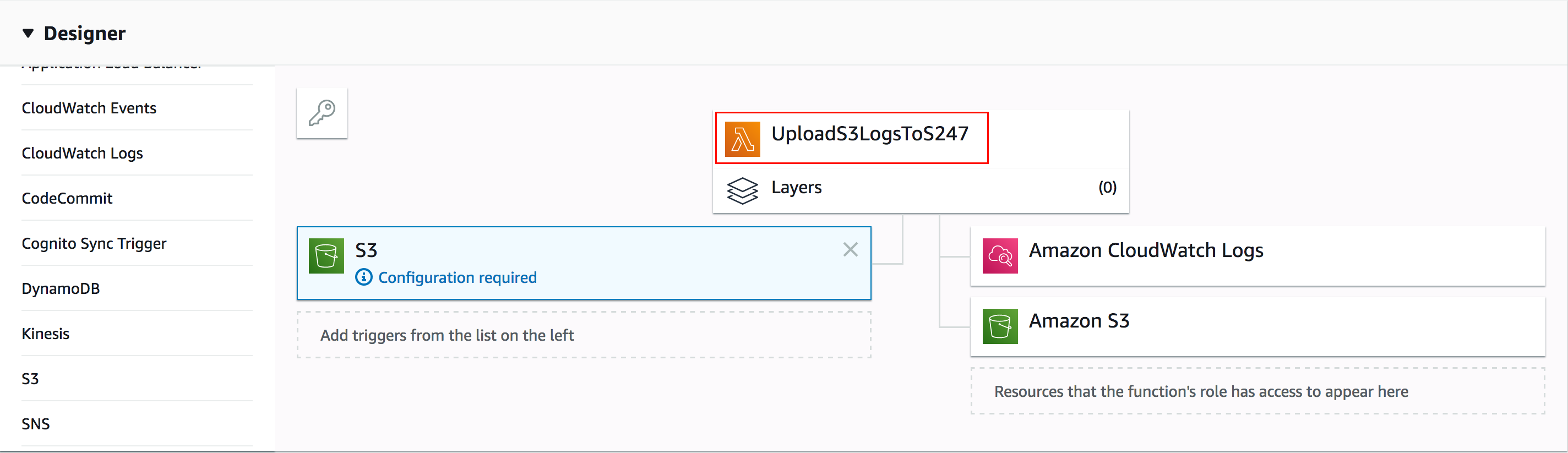
- Scroll to the editor, and place the code provided in the link below:
https://github.com/site24x7/applogs-aws-lambda/blob/master/s3/s3-sender.py
- After entering the code, navigate to the Site24x7 web client, select Admin > Applogs > Log Profile, then select the created Log Profile, and copy the code that appears on the screen.
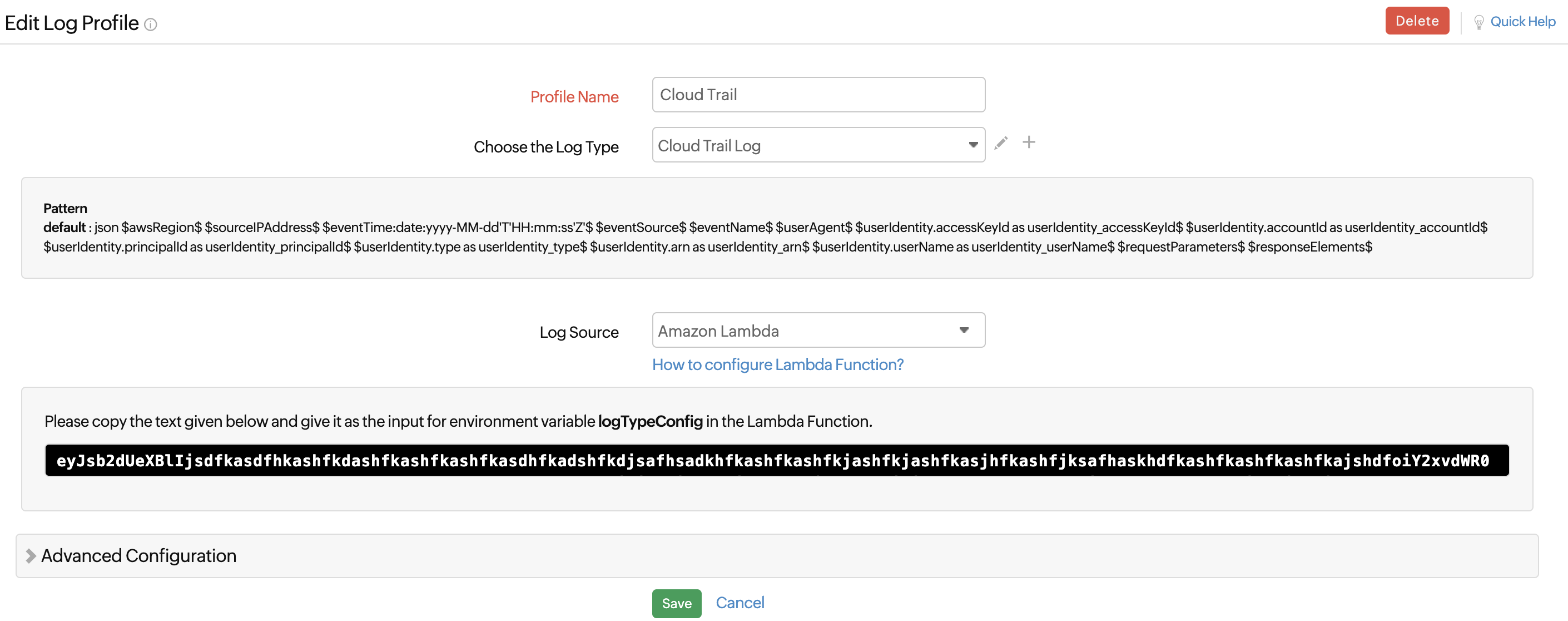
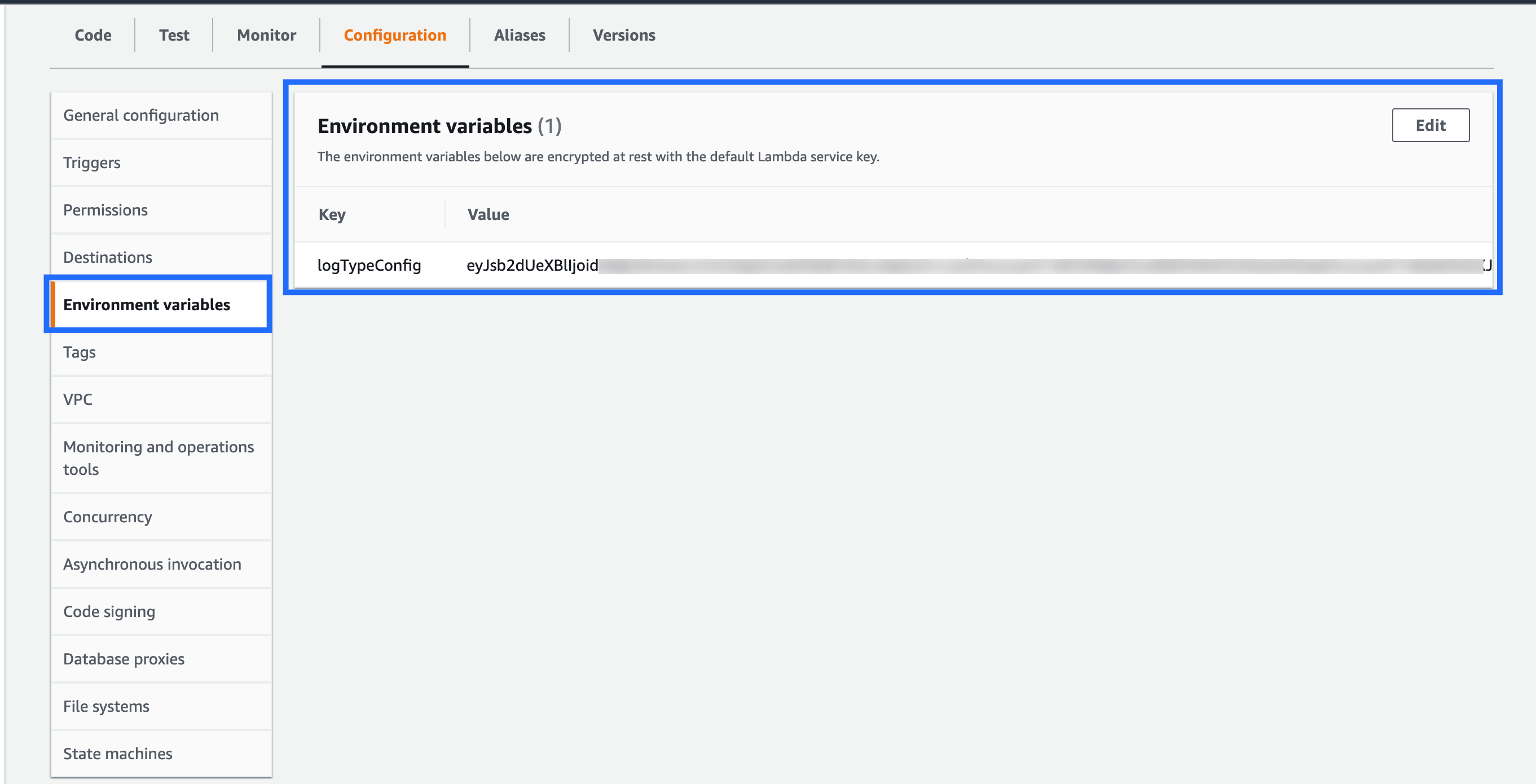
- Paste this code under Environment Variable with the field name logTypeConfig in the AWS console.
CloudTrail logs dashboard
AppLogs creates an exclusive dashboard for every Log Type, and shows a few widgets by default. Here's a list of the widgets available in the CloudTrail logs dashboard:
- Console Logins
- Failed Logons
- Top 10 Services
- Top 10 Events
- Active Users
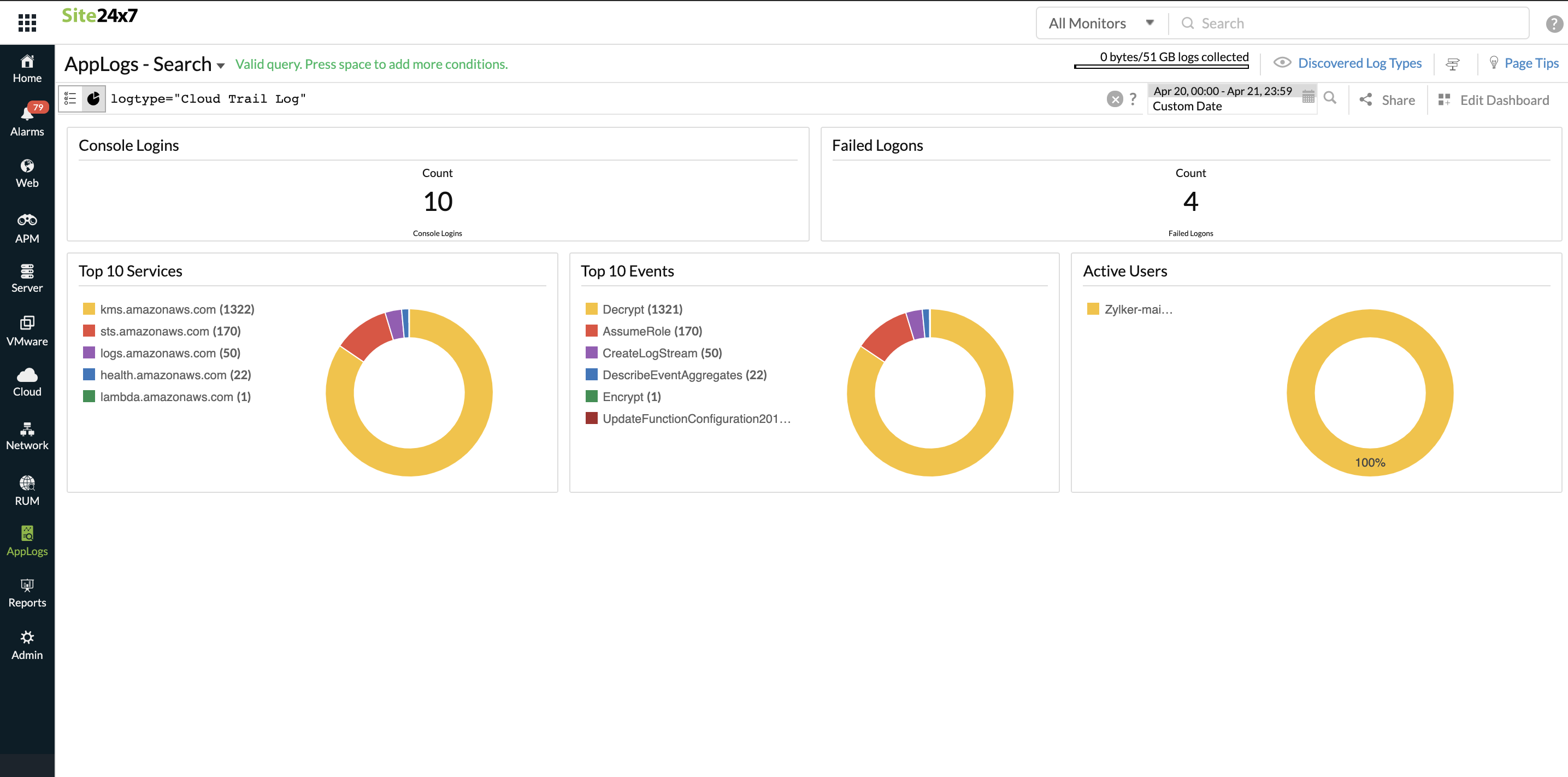
In addition to the default widgets, your saved searches will also be added to the dashboard automatically.